Credentials
follow the specific cloud and preferred method to create the necessary credentials below:
AWS
One Click Role
CLI
How Massdriver uses your role
To keep your environment secure, Massdriver uses a role with a trust policy to access your AWS account for provisioning and monitoring of your infrastructure. The account that assumes this role is private and has no access from the public internet.
Create a role with a trust policy
Run the following command with the AWS CLI. Replace <UUID HERE> with Loading.... Save it for importing the role in to Massdriver.
aws iam create-role --role-name=massdriver-provisioner --description="Massdriver Cloud Provisioning Role" --assume-role-policy-document='{"Version":"2012-10-17","Statement":[{"Sid":"MassdriverCloudProvisioner","Effect":"Allow","Principal":{"AWS":["308878630280"]},"Action":"sts:AssumeRole","Condition":{"StringEquals":{ "sts:ExternalId":"<UUID HERE>"}}}]}'
Assign the role administrator privileges
Fill in the role name used above and run this command to give Massdriver administrator privileges.
aws iam attach-role-policy --role-name={{ROLE_NAME}} --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
Import role to Massdriver
In the form to the left, name the credential as your AWS account for use within Massdriver and fill in both the aws arn as arn:aws:iam::YOUR_AWS_ACCOUNT_ID:role/{{ROLE_NAME}} and the external ID. Click submit and head to the projects page to start building your infrastructure.
Console
How Massdriver uses your role
To keep your environment secure, Massdriver uses a role with a trust policy to access your AWS account for provisioning and monitoring of your infrastructure. The account that assumes this role is private and has no access from the public internet.
Create a role
- Sign in to the AWS Management Console
- In the search bar, type
IAMand select the IAM service - In the left-hand menu, select
Roles - Click
Create role
- Select
Another AWS accountfor the role type
- For the account ID enter
308878630280. This is the Massdriver account which contains the role that will use the one you are creating now - Check the Require external ID box and enter Loading....
- Make sure that the Require MFA option is unchecked
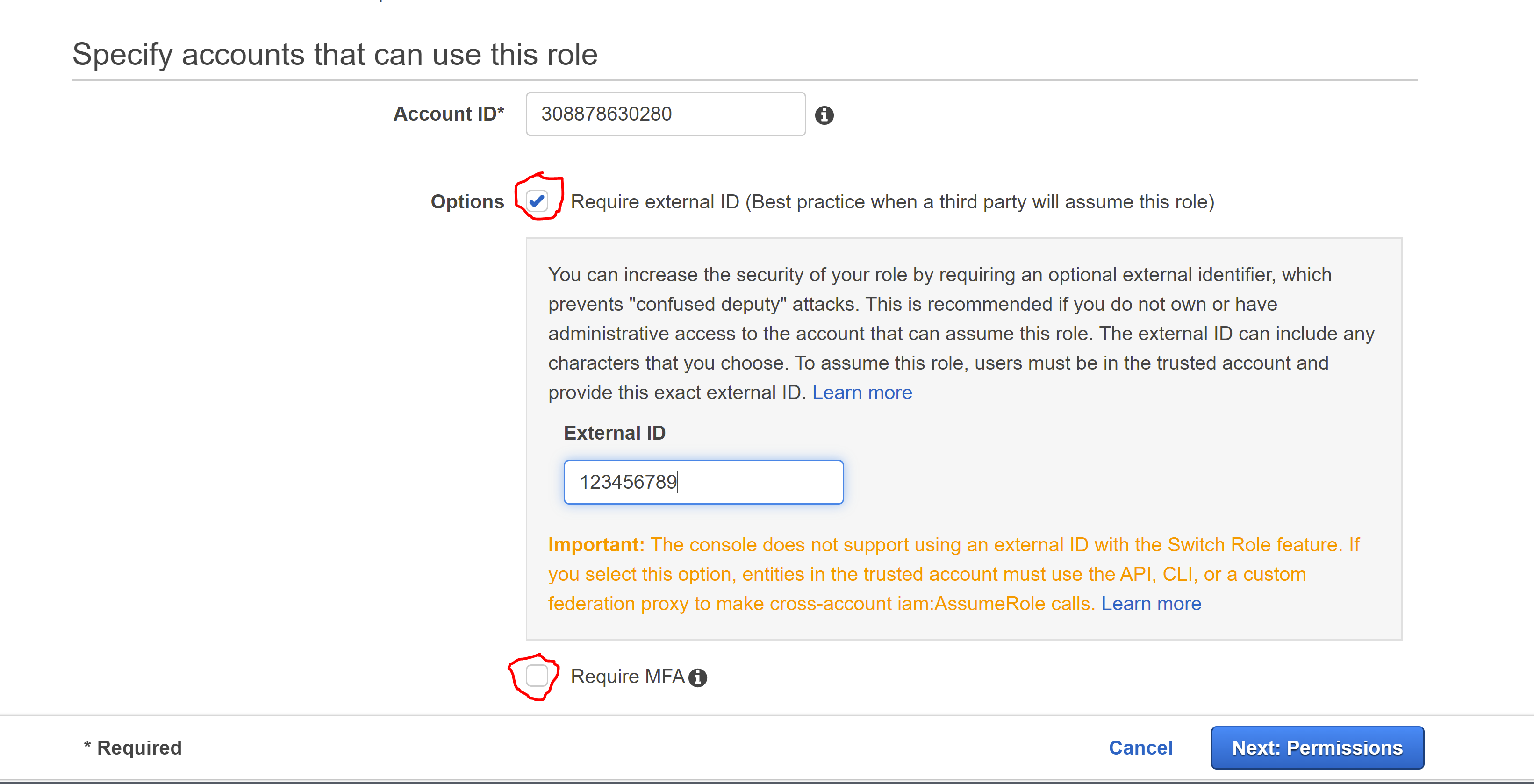
- Click "Next: Permissions"
- Select the
AdministratorAccesspolicy
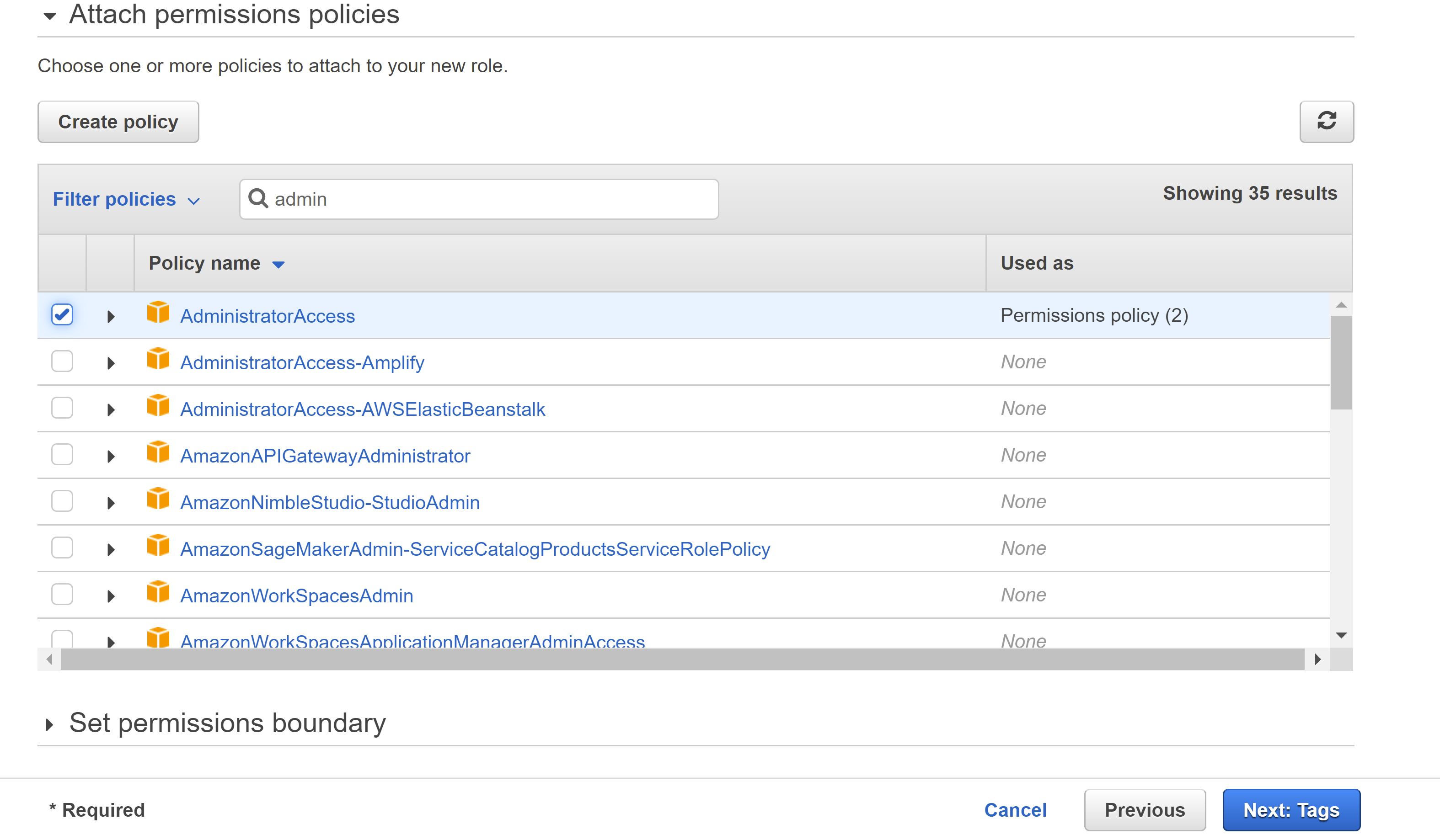
- Select
Next: Tags - Add a tag with the key
massdriver
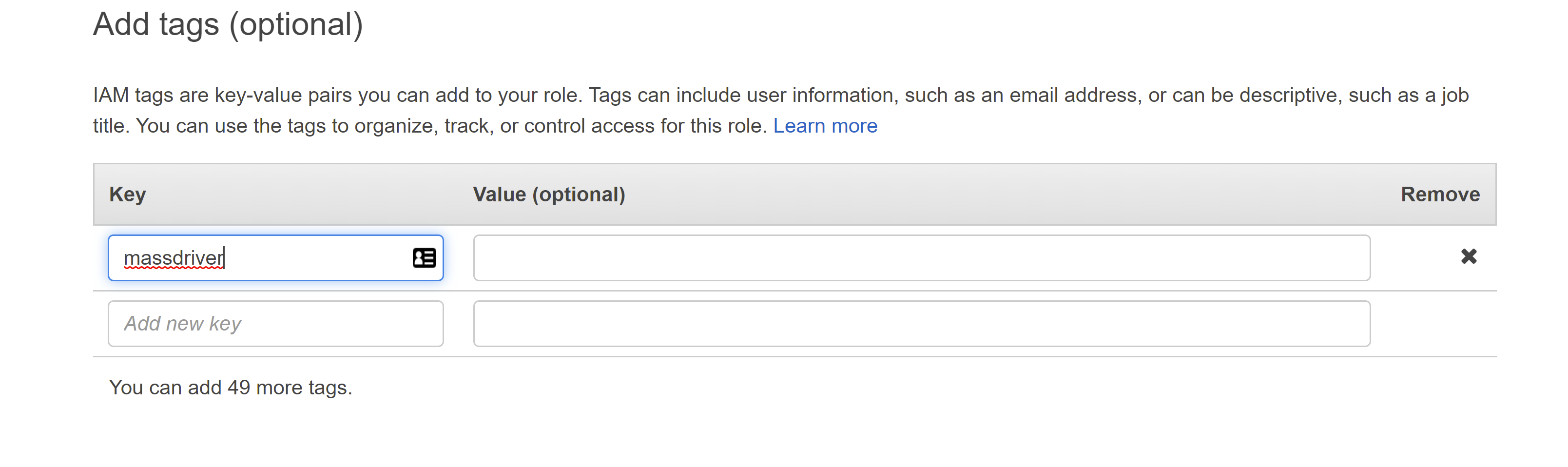
- Add a name and a description to the role. Save the role name for entry in to the form to the left
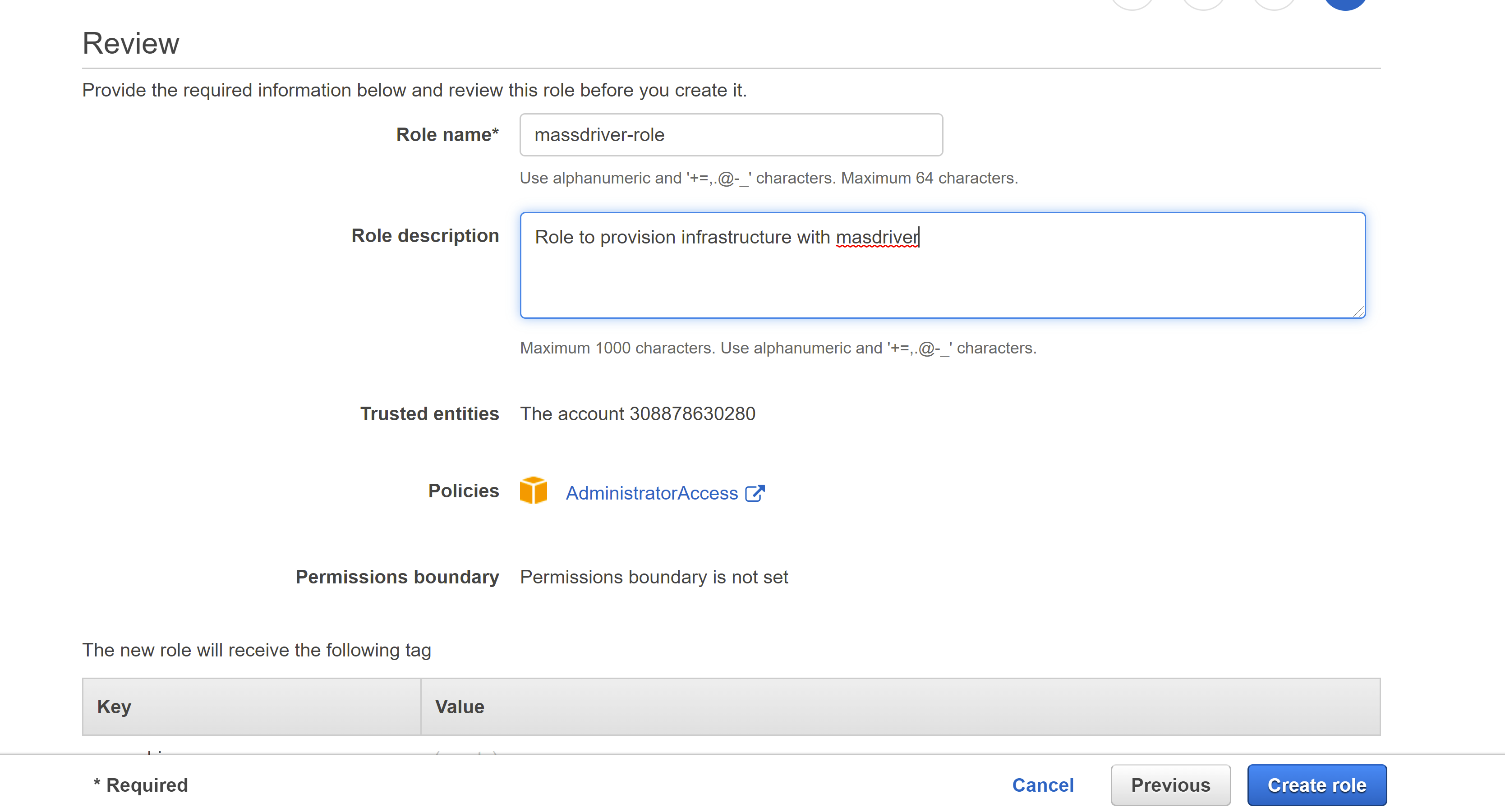
- In Massdriver, name the credential as your AWS account
- Paste the AWS arn for the role in the appropriate field with the format:
arn:aws:iam::YOUR_AWS_ACCOUNT_ID:role/ROLE_NAME
- If you haven't already paste your external ID in to the appropriate field
- Submit the role to Massdriver and head to the projects page to begin provisioning infrastruture.
Azure
CLI
Install Azure CLI
To get started, you'll need the Azure CLI installed locally on your machine. The Azure Cloud Shell available in the Azure Portal does not have the ability to grant the service principal the required permissions.
- Obtain your subscription ID
Paste this script into the command-line to list your subscriptions:
az account list --output table
Copy the value of the SubscriptionId and TenantId you want to use and paste it into Massdriver under Subscription ID and Tenant ID, and also store the SubscriptionId for the next step.
- Paste this script in the command-line to create an Azure service principal, and replace
<mySubscriptionID>with the subscription ID you copied from the last step:
az ad sp create-for-rbac --name massdriver-service-principal \
--role owner \
--scopes /subscriptions/<mySubscriptionID>
- Copy the following attributes and paste them into Massdriver:
- appId → Client ID
- password → Client Secret
Once finished, click the Submit button in Massdriver to create your credential.
Console
Registering the service principal app in Azure AD
- Sign into your Azure account through the Azure portal
- Search for and select Microsoft Entra ID
- Select App registration
- Select New registration
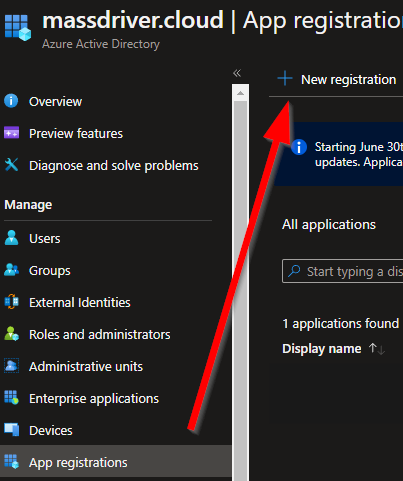
- Name your application:
massdriver-service-principal - Select Accounts in this organization directory only
- Leave Redirect URI blank
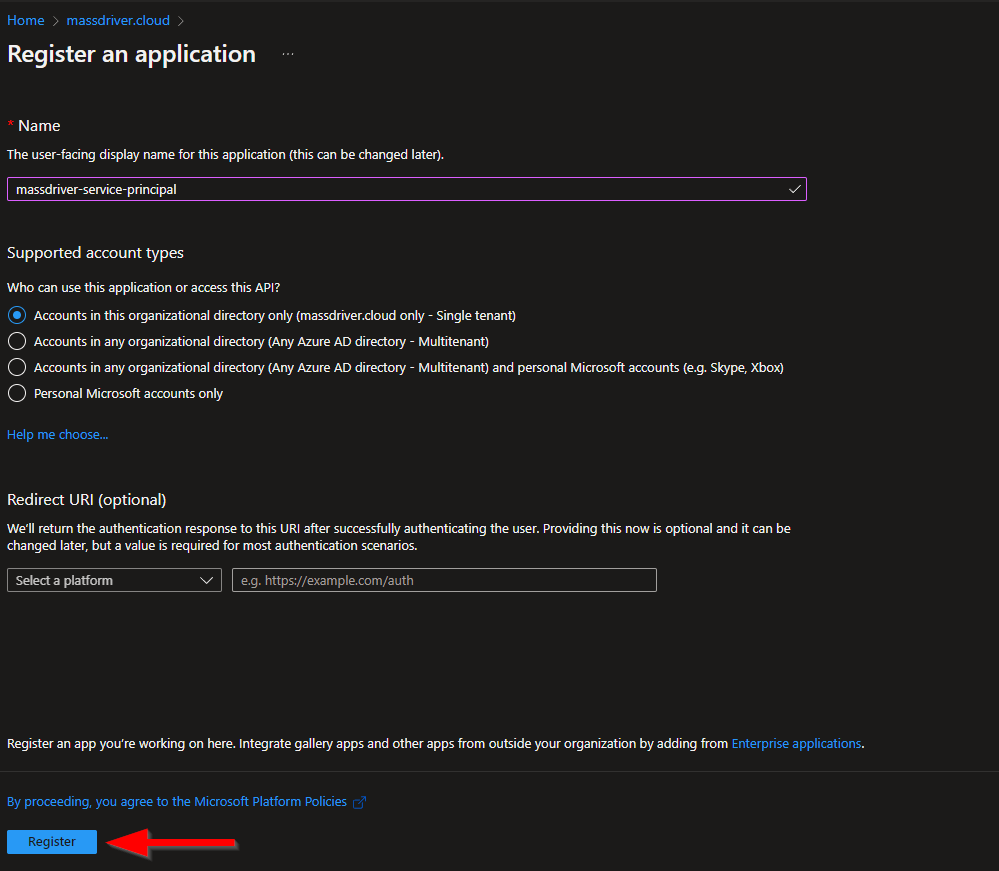
- Click Register
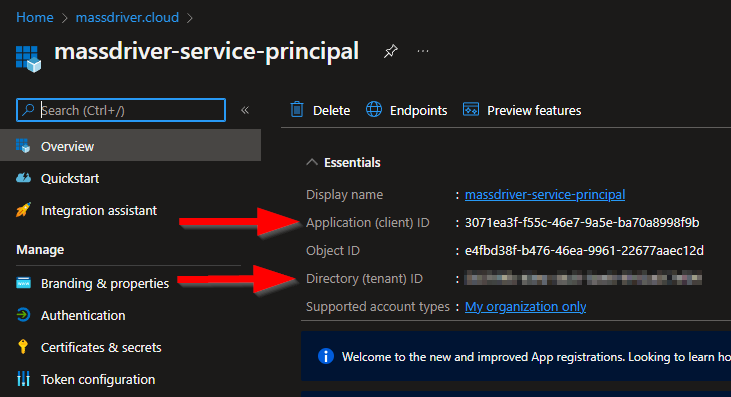
- On the Overview menu, copy the following values and paste them into Massdriver:
- Application (client) ID → Client ID
- Directory (tenant) ID → Tenant ID
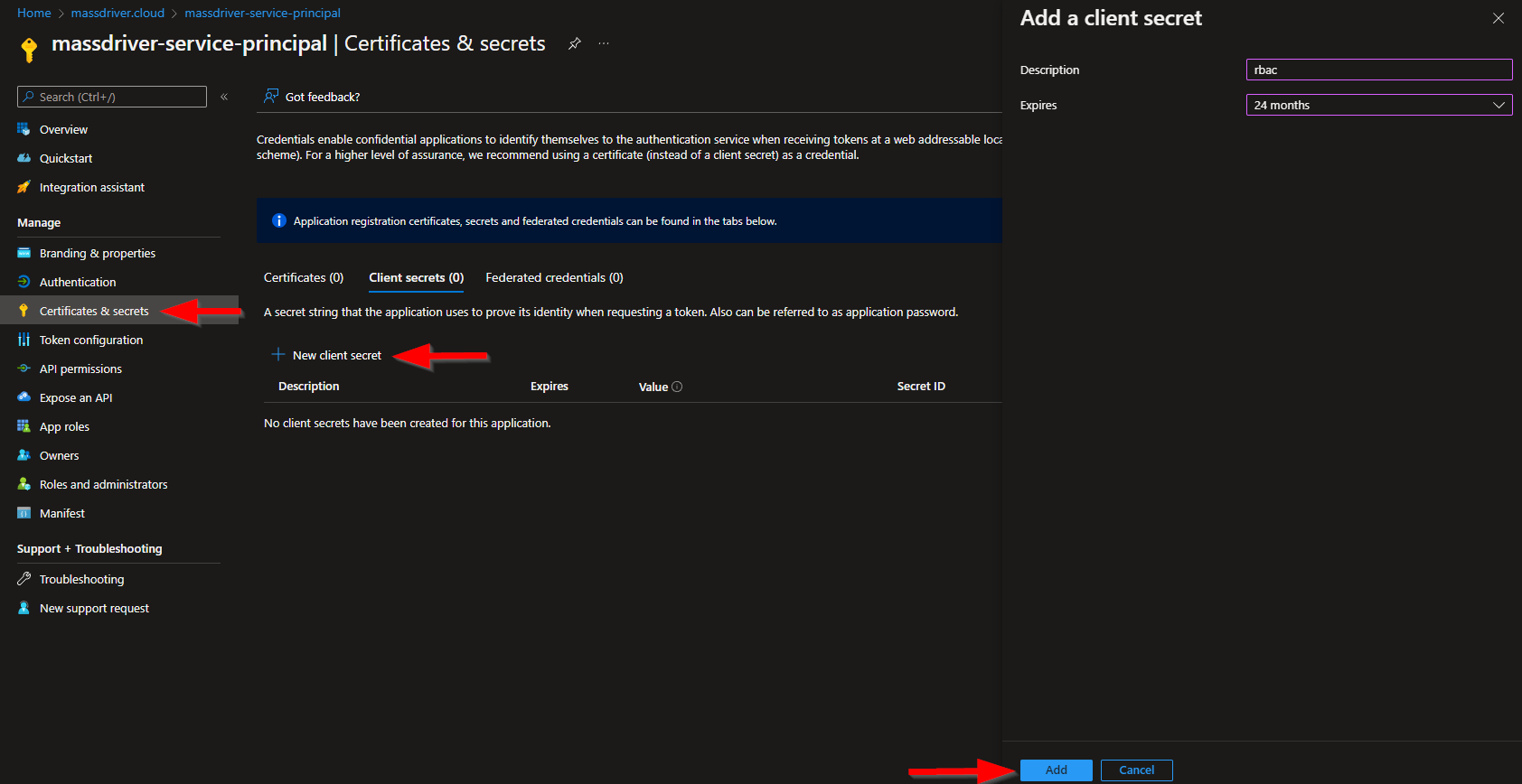
- Select Certificates & secrets on the left
- Select New client secret
- Set the description to
platform, set expiration date, and click Add
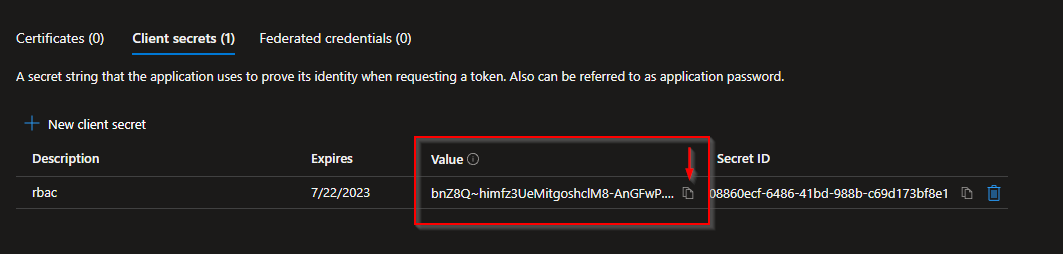
- Copy the Value password and paste into Massdriver under Client Secret. Do not use the Secret ID.
Assign subscription Owner the service principal
- In the Azure portal, search for and select Subscription
- Select the subscription you want to use in Massdriver
- In the Overview menu, copy your Subscription ID and paste it into Massdriver under Subscription ID
- Select Access control (IAM)
- Select Add > Add role assignment
- Select Privileged Administrator Roles tab and then the Owner role and click Next
- Select Select members, search for
massdriver-service-principal, click on the service principal, and then click Select at the bottom, then Next - Select Allow user to assign all roles except privileged administrator roles and click Next then Review + assign twice to finish.
Adding the Azure service principal to your Massdriver organization
- In Massdriver, click on the menu on the top left and expand Organization Settings
- Click Configure Credentials
- Select Azure Service Principal
- Set the credential name to your subscription name
- Fill in the fields as guided below:
- Client ID (appId in Azure CLI)
- Client Secret (service principal password)
- Subscription ID
- Tenant ID (tenant in Azure CLI)